In the realm of digital security, the potential vulnerability of our social media platforms is a topic that warrants serious consideration. Instagram, a popular platform for sharing memories and connecting with others, may not be immune to the risk of hacking, particularly through messages. This article delves into the intricate techniques employed by hackers to infiltrate Instagram accounts, explores signs of potential compromise, and offers practical steps to fortify your Instagram account against message-based attacks. Join us as we navigate the intricate landscape of digital security and safeguard our online presence.
Key Takeaways
- Hackers can infiltrate Instagram accounts through various methods such as phishing, fake websites, malicious links, brute force attacks, and exploiting vulnerabilities.
- Signs that your Instagram account may have been hacked include unusual account activity, changed password or email, being locked out of your account, unfamiliar connections or messages, and the need for immediate action.
- Hackers exploit vulnerabilities in Instagram messages through phishing attacks, social engineering techniques, and gaining access to sensitive information.
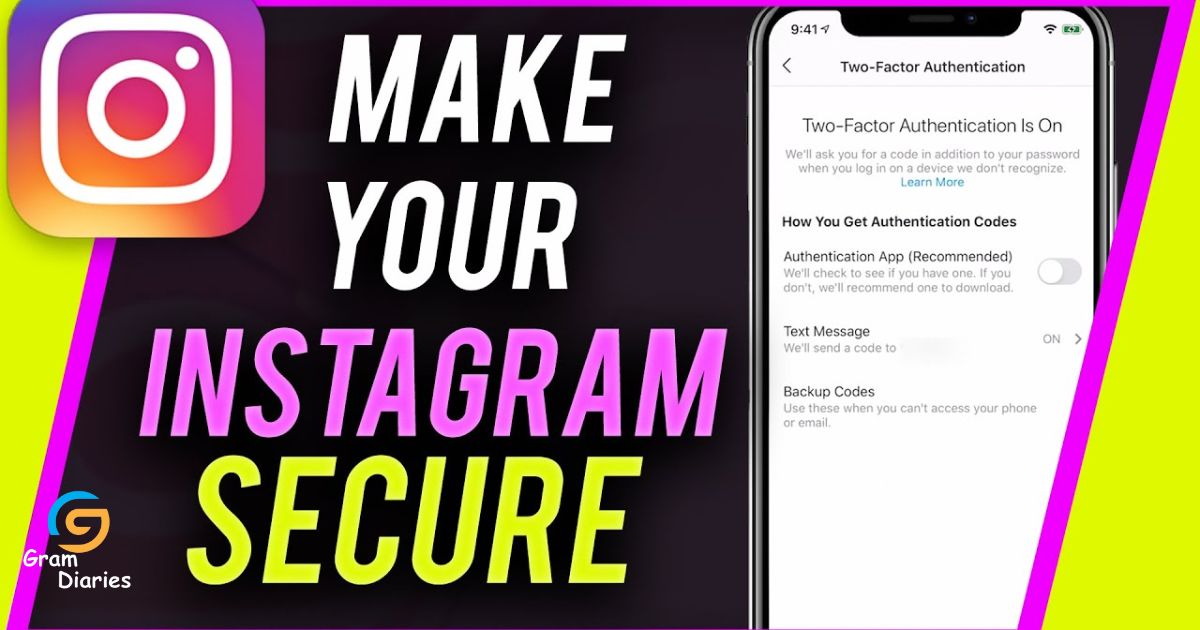
- To protect your Instagram account from message-based hacking, enable two-factor authentication, be cautious of suspicious messages, use a strong and unique password, regularly update your password, and understand the importance of strong passwords and two-factor authentication.
The Methods Hackers Use to Infiltrate Instagram Accounts
There are numerous methods that hackers employ to infiltrate Instagram accounts, making it imperative for users to be vigilant in protecting their personal information and account security. One common method is phishing, where hackers use deceptive tactics to trick users into revealing their login credentials. This can be done through fake websites that resemble the Instagram login page or through malicious links sent via messages. Another technique is brute force attacks, where hackers use automated software to guess the user’s password by trying different combinations. Additionally, hackers may exploit vulnerabilities in the Instagram platform itself, such as weaknesses in the code or insecure APIs. It is crucial for users to stay updated with the latest security measures and enable two-factor authentication to mitigate the risk of unauthorized access to their Instagram accounts.
Common Signs That Your Instagram Account May Have Been Hacked
If suspicious activity, such as unusual posts or unauthorized access, occurs on your Instagram account, it is crucial to take immediate action to secure your personal information and prevent further damage. Here are four common signs that your Instagram account may have been hacked:
- Unusual Account Activity: If you notice unfamiliar posts, comments, or messages on your account, it could be a sign of unauthorized access.
- Changed Password or Email: If you receive notifications about changes to your account password or email address that you did not initiate, it may indicate that someone else has gained control of your account.
- Locked Out of Account: If you are suddenly unable to access your account, despite entering the correct credentials, it could be a result of a hacker changing your login information.
- Unfamiliar Connections or Messages: If you notice new followers, messages from unknown accounts, or suspicious direct message requests, it is possible that your account has been compromised.
If you observe any of these signs, it is important to take immediate action by changing your password, enabling two-factor authentication, and reporting the incident to Instagram support.
How Hackers Exploit Vulnerabilities in Instagram Messages?
A significant number of hackers have been exploiting vulnerabilities in Instagram messages to gain unauthorized access to user accounts and compromise their personal information. Instagram, being one of the most popular social media platforms, has become a prime target for cybercriminals. Hackers employ various tactics, such as phishing attacks and social engineering techniques, to trick users into revealing their login credentials or clicking on malicious links. Once inside, they can access sensitive information, including private messages, photos, and even credit card details if saved. To protect against such attacks, users should be cautious when clicking on links or downloading attachments from unknown sources. Enabling two-factor authentication and regularly updating passwords are also essential to enhance security. Additionally, Instagram should continually monitor and patch vulnerabilities to prevent unauthorized access and safeguard user data. By being vigilant and taking necessary precautions, users can reduce the risk of falling victim to hackers and protect their online presence.
Steps to Protect Your Instagram Account From Message-Based Hacking
To effectively protect your Instagram account from message-based hacking, it is crucial to follow a series of proactive steps, such as regularly updating your password and enabling two-factor authentication. Here are four key measures you can take to enhance the security of your Instagram account:
- Enable two-factor authentication: This adds an extra layer of security by requiring a verification code in addition to your password when logging in.
- Be cautious of suspicious messages: Avoid clicking on links or downloading attachments from unknown senders, as they may contain malware or phishing attempts.
- Use a strong, unique password: Create a password that is complex and not easily guessable. Avoid using common words or personal information.
- Regularly update your password: Change your password periodically to prevent unauthorized access to your account.
Understanding the Importance of Strong Passwords and Two-Factor Authentication
Implementing strong passwords and utilizing two-factor authentication are essential for safeguarding sensitive information and preventing unauthorized access to online accounts. A strong password should be a combination of upper and lowercase letters, numbers, and special characters, making it difficult for hackers to guess. Two-factor authentication adds an extra layer of security by requiring users to verify their identity through a second method, such as a fingerprint or a unique code sent to their mobile device. By implementing these measures, users can significantly reduce the risk of their Instagram accounts being hacked. However, it is not enough to solely rely on these security measures. Users must also be vigilant in recognizing and avoiding suspicious messages and phishing attempts on Instagram, as hackers are constantly finding new ways to trick users into revealing their personal information.
Recognizing and Avoiding Suspicious Messages and Phishing Attempts on Instagram
In order to protect your Instagram account from potential hacking attempts, it is crucial to recognize and avoid suspicious messages and phishing attempts. Phishing scams often involve deceptive messages that appear to be from a legitimate source, tricking users into revealing sensitive information or downloading malicious software. By staying vigilant and being cautious of unexpected or suspicious messages, users can protect themselves against these types of cyber threats.
Identifying Phishing Scams
Users must remain vigilant in order to protect themselves from falling victim to phishing scams, as these fraudulent attempts can lead to stolen personal information and financial loss. Phishing scams are becoming increasingly sophisticated, making it essential for users to educate themselves on how to identify and avoid them. Here are four key factors to consider:
- Emails and messages: Be cautious of unsolicited emails or messages asking for personal information or urging immediate action. Legitimate organizations will never ask for sensitive information via email or message.
- URLs: Pay attention to the URL of any website you visit. Phishing websites often use slight variations or misspellings of legitimate URLs to deceive users. Always double-check the website’s legitimacy before entering any personal information.
- Grammar and spelling: Phishing emails often contain spelling mistakes, grammatical errors, or awkward phrasing. These mistakes can be an indication of a fraudulent attempt.
- Suspicious requests: Be cautious of any requests for passwords, financial information, or other sensitive data. Legitimate organizations will not ask you to provide such information unless you initiate the contact.
Protecting Against Hacking
One crucial aspect of safeguarding against hacking on Instagram is to actively monitor and promptly respond to any suspicious messages or phishing attempts that may arise. In today’s digital landscape, hackers are becoming increasingly sophisticated in their methods, making it essential for users to remain vigilant in protecting their accounts. By actively monitoring messages and being aware of common phishing techniques such as fake login pages or deceptive links, users can significantly reduce the risk of their account being compromised. Additionally, promptly responding to any suspicious activity or reporting it to Instagram can help mitigate potential damage. It is also important to regularly update passwords, enable two-factor authentication, and avoid sharing sensitive information through direct messages. By implementing these practices, users can enhance their account security and ensure a safe and enjoyable experience on Instagram.
The Role of Social Engineering in Instagram Hacking
The effectiveness of social engineering techniques in facilitating Instagram hacking has become a significant focus of the ongoing discussion. Social engineering refers to the manipulation of individuals to gain unauthorized access to sensitive information or accounts. In the context of Instagram hacking, social engineering techniques are employed to deceive users and trick them into revealing their login credentials or other personal information. Here are four key points to consider:
- Phishing attacks: Hackers send fraudulent messages or emails that appear legitimate, enticing users to click on malicious links or provide their login details.
- Impersonation: Hackers impersonate trusted individuals, such as friends or family members, to gain the victim’s trust and extract sensitive information.
- Pretexting: Hackers create false scenarios or reasons to convince users to disclose their login credentials or personal details.
- Baiting: Hackers offer attractive incentives or rewards to entice users into revealing their account information.
It is crucial to remain vigilant and cautious while interacting online to prevent falling victim to social engineering attacks.
Best Practices for Keeping Your Instagram Account Secure From Message-Based Attacks
An effective strategy to protect your Instagram account from message-based attacks is to implement the best practices recommended by cybersecurity experts. These practices include being cautious of unsolicited messages, especially those containing suspicious links or asking for personal information. It is important to verify the identity of the sender before responding or clicking on any links. Enabling two-factor authentication (2FA) adds an extra layer of security by requiring a verification code in addition to your password. Regularly updating your password to a strong and unique one is also crucial. Additionally, keeping your device’s operating system and Instagram app up to date ensures you have the latest security patches. By following these best practices, you can significantly reduce the risk of falling victim to message-based attacks and maintain the security of your Instagram account.
Frequently Asked Questions
How Can I Recover My Instagram Account if It Has Been Hacked Through Messages?
If your Instagram account has been hacked through messages, you can take several steps to recover it. This includes resetting your password, enabling two-factor authentication, reporting the incident to Instagram, and reviewing your account’s security settings.
Can a Hacker Access My Personal Information Through a Hacked Instagram Account?
A hacker can potentially access personal information through a compromised Instagram account. It is crucial to ensure strong security measures, such as using unique passwords and enabling two-factor authentication, to mitigate the risk of unauthorized access.
Are There Any Warning Signs That My Instagram Account May Be Compromised Even if I Haven’t Received Any Suspicious Messages?
If you suspect that your Instagram account may be compromised, it is essential to look for warning signs even if you haven’t received any suspicious messages. These signs can include unauthorized account activity, unfamiliar followers, or changes in profile settings.
Can Instagram’s Two-Factor Authentication Feature Prevent Message-Based Hacking?
Instagram’s two-factor authentication feature provides an additional layer of security to prevent unauthorized access to accounts. By requiring a verification code in addition to a password, it significantly reduces the risk of message-based hacking.
What Should I Do if I Receive a Suspicious Message on Instagram?
If you receive a suspicious message on Instagram, it is important to exercise caution. Avoid clicking on any links or providing personal information. Report the message to Instagram and consider enabling two-factor authentication for added security.
Conclusion
In conclusion, it is essential to remain vigilant and take necessary precautions to protect your Instagram account from message-based hacking. By understanding the methods used by hackers, recognizing signs of a compromised account, and implementing strong passwords and two-factor authentication, users can significantly reduce the risk of falling victim to these attacks. Additionally, being cautious of suspicious messages and avoiding social engineering tactics can further enhance the security of your Instagram account. It is crucial to prioritize account security to maintain a safe online presence.